KEYPO BLOG
Insights on cryptocurrency security, self-custody, and protecting your digital assets.

Reflections from the Node Foundation Opening: NFTs, Security, and the Future of Self-Custody
Last weekend, the Node Foundation opened its headquarters in Palo Alto. The three-day event was a celebration of NFTs and digital art, and offered key takeaways on seed phrase security and self-custody.
The Future of Ethereum Wallets: Why EIP-7951 Doesn't Mean the End of Seed Phrases
The Fusaka upgrade brought EIP-7951 and P-256 precompiles to Ethereum, enabling passkey wallets. But seed phrases aren't going anywhere—we're entering an era that demands more sophisticated approaches to wallet security.
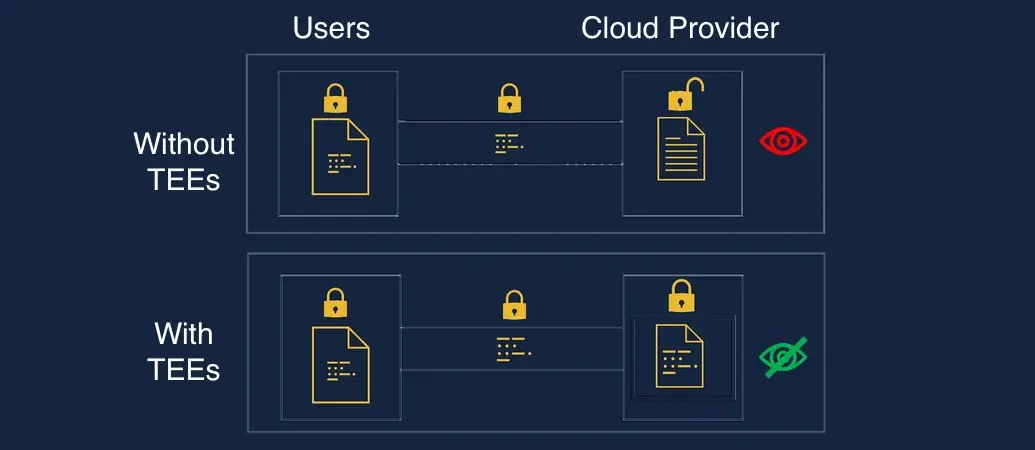
Inside Trusted Execution Environments: Architecture, Applications, and Attack Vectors
TEEs have become a cornerstone of modern cryptographic security infrastructure, powering everything from Apple Pay to confidential cloud computing. But recent reports have exposed critical vulnerabilities that every developer and security professional needs to understand.
Understanding TEE Security: Why Physical Attacks Matter Differently for Cloud vs. Consumer Devices
Trusted Execution Environments offer excellent protection against software attacks, but their physical attack resilience varies dramatically between cloud and consumer implementations.